Cozy Bear’s Wine Lure Drops WineLoader Malware on EU Diplomats

Midnight Blizzard (APT29/Cozy Bear) targets European embassies and Ministries of Foreign Affairs with sophisticated phishing emails disguised as wine tasting invitations. Learn about the new GrapeLoader malware and the updated WineLoader backdoor deployed in this campaign.
The notorious group of Russian government-backed hackers from the Midnight Blizzard, APT29, or Cozy Bear, have been attempting to infiltrate European diplomats’ computer systems since January, sending out fake emails to embassies and diplomatic organisations across Europe.
Researchers at Check Point Research (CPR), who have been tracking this activity, discovered that hackers are using a new malware called ‘GrapeLoader’ to gain entry, followed by installing an updated, sneakier version of a backdoor program called ‘WineLoader’ once inside.
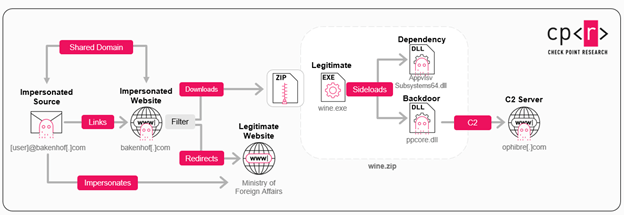
The attack starts with emails that look like they are official invitations from a country’s Ministry of Foreign Affairs, inviting people to wine tasting events. Check Point’s analysis showed that almost all the emails used the theme of wine-tasting events, and if the first email fails, the hackers send more to trick the user.
This campaign “appears to be a continuation of a previous one that utilised a backdoor known as WINELOADER,” documented by Zscaler in February 2024.
The emails, sent from two website addresses, bakenhofcom and silrycom, contains a malicious link that initiates the download of a file named “wine.zip.” When opened, it runs three files, including a disguised file called “ppcore.dll” that acts as the GrapeLoader program.
GrapeLoader copies the contents of the “wine.zip” file to a new location on the computer’s hard drive and changes the computer’s settings to automatically run a program called “wine.exe” every time the computer is turned on, ensuring the hackers maintain their access. It must be noted that hackers are specifically targeting European Ministries of Foreign Affairs and embassies.
The WineLoader backdoor is a sophisticated tool designed to gather sensitive information from infected computers, aiding hackers in their cyber spying operations. Researchers discovered that this new version is harder to detect due to its code-hiding techniques, whereas its older versions were comparatively easier to analyse with automated tools.
The backdoor collects information such as the computer’s IP address, program name, Windows username, and process ID. This backdoor has been used in previous hacking attempts by Midnight Blizzard against diplomats, CPR highlighted in their blog post.
Researchers describe GrapeLoader as a relatively new tool used in the early stages of this attack to gather information about the infected computer, ensure hackers can maintain access, and download the next stage of their attack, the WineLoader backdoor. GrapeLoader uses various tricks to avoid detection by security tools, such as hiding text within its code and finding necessary computer functions at runtime.
The operation highlights the evolving nature of cyber espionage and the persistent threat posed by nation-state actors to diplomatic communications and systems. This discovery serves as a reminder for diplomatic organisations to remain alert, implement stronger cybersecurity measures, and educate personnel about the risks of sophisticated phishing attacks.
HackRead